Best Practices for Data Destruction to Strengthen Your Cyber Security Structure
Best Practices for Data Destruction to Strengthen Your Cyber Security Structure
Blog Article
How Proper Information Devastation Adds To Robust Computer Safety Providers and Mitigates Risks of Data Breaches
In today's electronic landscape, the significance of proper data destruction can not be overemphasized, as it serves as a basic element of detailed computer system safety and security services. The ramifications of insufficient data devastation extend beyond simple compliance; they can profoundly impact an organization's cybersecurity pose and track record.
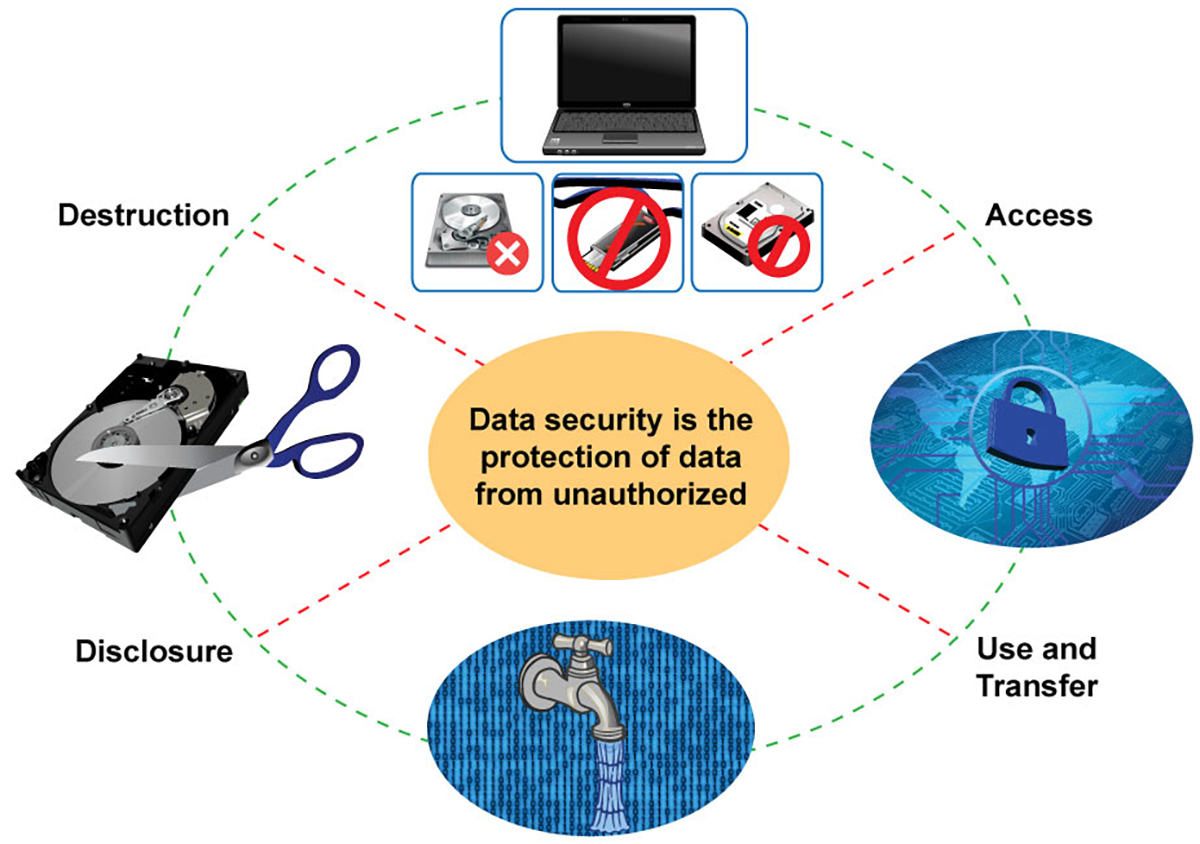
Significance of Information Devastation
In today's electronic landscape, the relevance of data destruction can not be overstated. As organizations progressively depend on electronic properties, the possible threats related to information violations and unapproved access amplify. Effective data destruction is a vital element of a detailed details protection approach, safeguarding sensitive information from coming under the hands of destructive stars.
When information is no more needed, just deleting files or formatting hard disks wants. Recurring information can commonly be recovered using easily offered tools, positioning significant threats to both people and companies. This emphasizes the requirement for robust data devastation methods that guarantee all data is irretrievably gotten rid of.
In addition, regulative compliance requireds, such as GDPR and HIPAA, stress the responsibility to protect delicate data, including its proper disposal. Non-compliance can bring about serious legal effects and punitive damages. data destruction. Therefore, integrating efficient data devastation protocols not just enhances security however also strengthens an organization's online reputation and credibility

Methods of Secure Data Erasure
Numerous efficient approaches of protected information erasure can be employed to make sure that sensitive info is completely eliminated from storage space devices. One commonly identified technique is data overwriting, which includes changing existing data with arbitrary patterns multiple times. This approach considerably minimizes the chances of information recovery, although it may not be effective versus sophisticated forensic strategies.

Physical devastation is also a dependable method, where storage gadgets are made unusable with shredding, squashing, or incineration. This approach ensures that data can not be recuperated by any kind of methods yet calls for mindful handling of unsafe products.
Lastly, specialized software program tools made for safe and secure data erasure offer functionalities that abide by different erasure criteria. These tools usually consist of features like verification procedures to validate successful data destruction.
Using these approaches in combination can enhance data protection and minimize the dangers connected with data violations, making sure that sensitive details is not accidentally subjected.
Legal and Compliance Factors To Consider
The techniques employed for safe data erasure not just serve to secure sensitive info but additionally must straighten with legal and conformity structures regulating information protection. Organizations are needed to adhere to different laws, such as the General Data Security Law (GDPR), the Health And Wellness Insurance Mobility and Liability Act (HIPAA), and the Payment Card Market Information Safety And Security Criterion (PCI DSS) These regulations mandate certain methods for data managing and devastation, ensuring that delicate and individual data is irretrievably eliminated when no more needed.
Failing to follow these legal needs can lead to considerable fines, including fines and reputational damage. Furthermore, companies have to maintain records of data damage procedures, showing conformity throughout audits or examinations. This documents not just protects against legal consequences however likewise strengthens trust fund with stakeholders and customers, showcasing a dedication to information protection.
Incorporating lawful and conformity factors to consider right into information devastation techniques is essential for any organization. It minimizes the risk of data violations and highlights an aggressive strategy to guarding delicate info, eventually promoting a culture of security and accountability throughout the company.
Influence On Cybersecurity Pose
Efficient website here data devastation dramatically boosts a company's cybersecurity position by decreasing the potential strike surface area for cyber risks. When sensitive information is not appropriately ruined, it remains obtainable to destructive actors who can exploit this info for unapproved accessibility, identity burglary, or business espionage. By click here to find out more applying robust information damage methods, organizations can efficiently minimize the threat of data violations and improve their total safety framework.
In addition, the protected disposal of outdated or unneeded data not only protects sensitive details however additionally assists companies adhere to sector policies and criteria. Failure to appropriately ruin information can result in extreme legal consequences and reputational damages, further jeopardizing an organization's cybersecurity stance.

Ultimately, prioritizing effective data destruction is crucial for cultivating a durable cybersecurity posture, making sure that organizations remain watchful against developing cyber risks while safeguarding their vital possessions and stakeholders.
Finest Practices for Organizations
Carrying out finest methods for data destruction is crucial for companies aiming to guard delicate details and alleviate cybersecurity dangers. Companies must establish an extensive data devastation policy that describes treatments and duties. This plan ought to adhere to pertinent guidelines, such as GDPR or HIPAA, guaranteeing lawful consistency.
Secondly, it is vital to utilize approved information sanitization techniques, including information wiping, degaussing, and physical devastation, tailored to the kind of data and storage space tool. Utilizing certified specialists for data devastation services boosts the reliability of these approaches.
Additionally, companies ought to keep a comprehensive supply of all data storage space devices, making sure that all obsolete or replaced tools undergoes damage. Regular audits of data devastation practices can assist boost and recognize weaknesses conformity.
Staff member training is another critical element, as staff should understand the value of information destruction and follow developed protocols. Organizations must record all information devastation tasks to give accountability and traceability, which can be very useful throughout audits or in the occasion of a violation.
Verdict
One commonly identified strategy is information overwriting, which entails changing existing data with random patterns multiple times.The approaches employed for safe data erasure not just offer to safeguard delicate details yet additionally must straighten with legal and compliance structures regulating information defense. These guidelines mandate details procedures for data handling and damage, making certain that individual and delicate data is irretrievably erased when no longer required.
By implementing durable information devastation procedures, organizations can effectively minimize the threat of data breaches and improve their total security framework.
In final thought, appropriate data damage is essential for enhancing computer security services and reducing the dangers associated with information breaches. - data destruction
Report this page